Cyber Risk Management: Safeguarding Businesses in the Digital Age
Dhiren M | 27 Aug 2025 | 28 Aug 2025
In today’s hyper-connected world, businesses depend on digital technologies more than ever. So, in the era of advanced technology dependencies, what is your thought on cyber risk management? From cloud adoption to mobile-first workplaces, every advancement comes with hidden vulnerabilities. Cyberattacks, ransomware, phishing scams, and third-party breaches are becoming routine headlines. The financial and reputational consequences of such attacks are devastating IBM’s 2023 Cost of a Data Breach report revealed that the average global cost of a breach is USD 4.45 million.
To counter these risks, organizations must adopt cyber risk management (CRM) as a structured and continuous process. It is no longer a support function; it is a strategic business enabler. By embedding cyber risk management frameworks and best practices, organizations can stay resilient, maintain compliance, and win customer trust in an increasingly hostile digital landscape.
“Let’s dive deeper into how cyber risk management (CRM) can become your organization’s strongest line of defense.”
What is Cyber Risk Management?
Cyber Risk Management is the ongoing practice of spotting potential digital threats, estimating their impact, and taking deliberate steps to minimize them. Unlike traditional IT security that only focuses on technology, it brings together policies, governance, and culture to safeguard the organization. The goal is simple, make sure that business operations continue smoothly even if cyber incidents occur.
Why Cyber Risk Management is Essential
The cyber threat landscape has evolved dramatically:
- Ransomware attacks have increased by almost 95% globally over the past five years.
- Third-party breaches now cause more than half of all data leaks, according to Ponemon Institute.
- Regulatory demands like GDPR, HIPAA, and India’s Digital Personal Data Protection Act (DPDPA) hold businesses legally accountable for poor risk practices.
Without a strong cyber risk management program, organizations face downtime, lawsuits, and reputational harm that can take years to recover from.
The Cyber Risk Management Framework
A cyber risk management framework works like a blueprint. It gives businesses a structured way to find risks, assign them priority, and apply controls that keep threats under check.
A good framework blends assessment, measurement, expert consulting, and third-party oversight into a single process. This makes decision-making less about guesswork and more about facts. 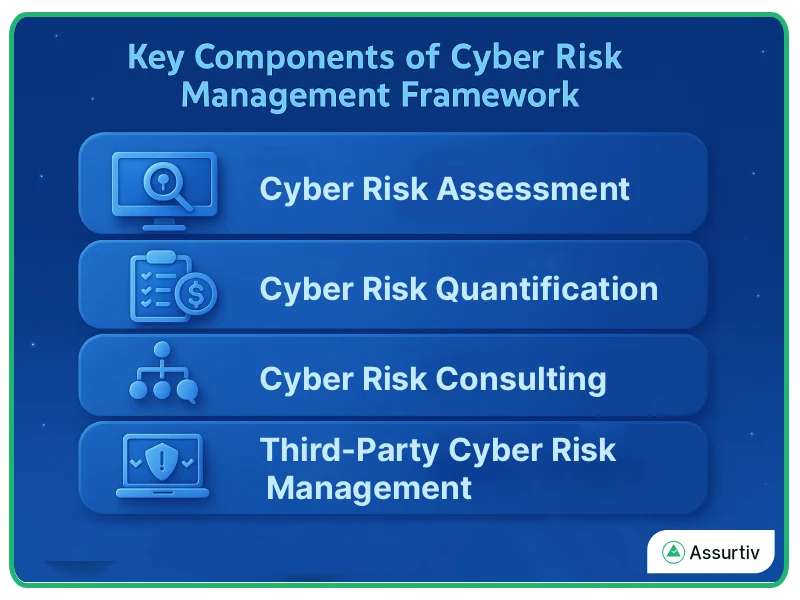
Key Components of a Framework
- Cyber Risk Assessment – Identifying critical assets, analysing threats, and rating vulnerabilities.
- Cyber Risk Quantification – Converting risks into measurable financial terms.
- Cyber Risk Consulting – Leveraging external expertise to design strategies that align with business needs.
- Third-Party Cyber Risk Management – Monitoring vendors, suppliers, and partners who may introduce hidden risks.
When a framework is in place, companies can better answer both how to measure cyber risk and how to reduce cyber risk.
Building a Cyber Risk Management (CRM) Program
A CRM program takes the framework off paper and puts it into practice. It is not a one-off project but a living process that updates with changing threats. By weaving risk awareness into everyday operations, such programs make security a shared responsibility- from leadership to employees to external vendors.
Core Elements of a Program
- Risk Identification – Mapping out critical systems and sensitive data.
- Risk Analysis – Understanding both the probability and consequences of incidents.
- Risk Prioritization – Ranking threats to focus on what matters most.
- Control Implementation – Deploying safeguards like access controls, encryption, and incident playbooks.
- Continuous Monitoring – Tracking risks in real time with security dashboards.
- Governance & Reporting – Communicating the organization’s risk posture to executives, auditors, and regulators.
Since most companies rely heavily on vendors for cloud hosting, payments, and IT services, third-party cyber risk management is one of the most critical pillars of a program.
CRM Best Practices
Organizations at different maturity levels can still follow cyber risk management (CRM) best practices to strengthen resilience:
- Run cyber risk assessments regularly to spot emerging vulnerabilities.
- Use cyber risk quantification to communicate risks in business language.
- Invest in cyber risk consulting for unbiased guidance and benchmarking.
- Apply third-party CRM processes to vendors and contractors.
- Integrate compliance management into the security cycle.
- Train employees often, since phishing remains a leading cause of breaches.
- Conduct incident simulations and penetration tests to evaluate readiness.
How to Measure Cyber Risk
One of the toughest boardroom questions is: how to measure cyber risk?
Here are the most common approaches:
- FAIR Model (Factor Analysis of Information Risk) – Converts risk into monetary values.
- Scenario Testing – Evaluates “what-if” situations like ransomware or insider threats.
- Risk Scoring – Assigns values to vulnerabilities and assets for prioritization.
- Key Risk Indicators (KRIs) – Tracks metrics like patching delays, phishing response rates, or failed login attempts.

By turning risks into measurable numbers, leaders can justify investments and prioritize security measures effectively.
How to Reduce Cyber Risk
Once measurement is clear, the next step is how to reduce cyber risk. The answer lies in layered defence and a mix of technical and organizational measures.
Practical Risk Reduction Strategies
- Adopt Zero Trust Architecture – Never trust; always verify.
- Stay on top of patches – Apply updates promptly across all systems.
- Enable Multi-Factor Authentication (MFA) – Prevent unauthorized logins.
- Encrypt data – Secure information in storage and during transfer.
- Vendor Due Diligence – Evaluate supplier compliance and risk history.
- Ongoing Employee Training – Educate staff to avoid human-error loopholes.
- Automated Monitoring – Use security tools that trigger alerts for unusual activity.
Together, these measures make risk management proactive instead of reactive.
Case Example: The Cost of Weak Risk Management
In 2024, a 158-year-old UK firm collapsed because of a weak password compromise that spiralled into a financial disaster. A single avoidable oversight brought down a legacy business.
This story highlights the importance of cyber risk assessments and awareness programs. Ignoring even simple risks can destroy years of brand value.
The Future of Cyber Risk Management
Emerging technologies are reshaping how organizations manage risk:
- Artificial Intelligence (AI) is predicting and detecting attacks faster than human teams.
- Blockchain is enhancing authentication and secure transactions.
- Cloud-native GRC solutions are enabling real-time monitoring across global operations.
The future belongs to businesses that treat risk management as a competitive advantage rather than a compliance burden.
Final Thoughts
Cyber threats are inevitable, but damage is not. By adopting Cyber Risk Management frameworks, programs, and best practices, organizations can prepare for the worst while enabling the best.
From cyber risk quantification to third-party cyber risk management, the focus should always be on building resilience. The businesses that thrive tomorrow will be those that treat cyber risk as a strategic priority, not just an IT issue.



