Data Breach: Meaning, Examples, and How to Stay Protected
Dhiren M | 28 Oct 2025 | 4 Feb 2026
In today’s digital world, information is the new currency. Every time you log in, make a purchase, or sign up on a website, your personal data travels across the internet. But what happens when that information is stolen or leaked? That’s called a data breach.
A data breach is one of the biggest risks in the digital age. It can affect individuals, companies, and even governments. Let’s explore what a data breach means, how it happens, and how you can protect yourself and your business from it.
What Is a Data Breach?
A data breach happens when sensitive, protected, or confidential data is accessed, shared, or stolen without permission. The stolen data may include personal details like your name, email, phone number, or password. Sometimes it involves financial records, medical history, or business secrets.
In simple terms, a data breach in cyber security is when someone breaks into a digital system and steals valuable information. The reasons can vary, from human error to hacking or system vulnerabilities. But the result is the same: lost data and broken trust.
Common Causes of Data Breach
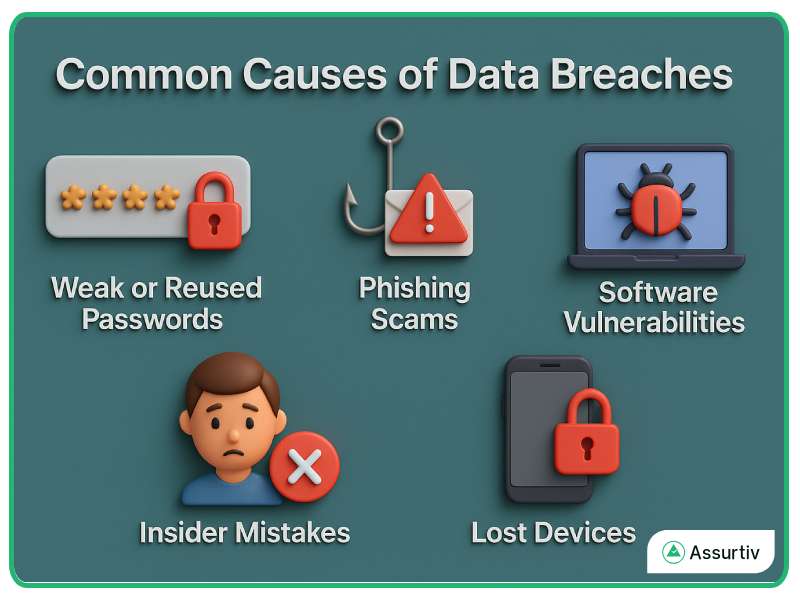 There is no single cause of a data breach. In most cases, multiple factors come together. Here are some common reasons why data breaches occur:
There is no single cause of a data breach. In most cases, multiple factors come together. Here are some common reasons why data breaches occur:
Weak or Reused Passwords
Many people still use simple passwords like “123456” or “password.” Hackers can easily guess them by using password-cracking tools. So, we recommend that you always use strong, unique passwords.
Phishing Scams
Phishing is a trick used by cybercriminals. They send fake emails that look real and ask you to click links or download files. Once you do, they get access to your system.
Software Vulnerabilities
Old software often has bugs or weaknesses. Hackers use these loopholes to get into your system. Regular updates can protect your devices from such attacks.
Insider Mistakes
Not all data breaches are caused by outsiders. Sometimes, employees accidentally share confidential data or click on harmful links.
Lost Devices
If you lose your phone or laptop without encryption, anyone who finds it can access your data. The best practice is always to lock and encrypt your devices.
Data Breach Examples in Recent Times
To understand how serious data breaches can be, let’s look at some of the recent data breach examples from the real world:
- Chinese Surveillance Network breach: Exposed 4 billion records, making it one of the largest in history.
- Power School breach: A contractor’s stolen login credentials led to the compromise of data for over 62 million students and nearly 10 million teachers.
- Yale New Haven Health System breach: A ransomware attack exposed the personal and medical data of over 5.5 million people.
- Santander Bank breach: Data from 30 million customers, including financial and personal information, was stolen, with researchers linking it to a larger breach at a cloud storage company named Snowflake.
- Change Health care breach: A ransomware attack, possibly initiated by a phishing email, is considered the largest healthcare breach ever, impacting an estimated 190 million individuals and significantly disrupting healthcare services nationwide.
- Google / Salesforce third-party breach: Attackers gained access to third-party systems like Salesforce, affecting several companies and exposing business contact information through social engineering.
- Air France -KLM breach: This incident was also traced back to third-party vulnerabilities, with hackers using social engineering to access company data.
- Transunion breach: Another company hit by the Shiny Hunters group, which exploited third-party platforms like Salesforce and Drift.
- Microsoft Share point servers: A zero-day vulnerability was exploited, impacting numerous businesses, government agencies, and universities.
These data breaches list shows that even major companies with strong cyber security systems are not immune. It proves why awareness and protection are crucial.
Impact of Data Breaches
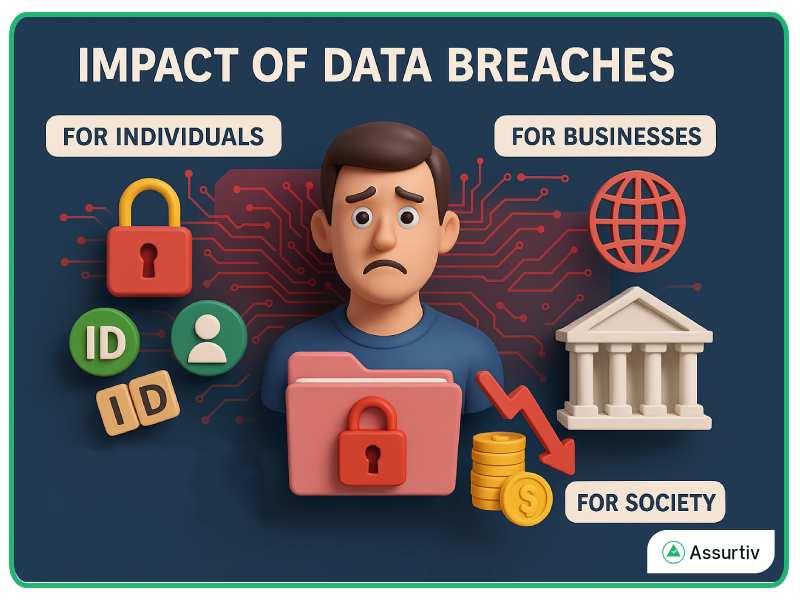 A data breach can cause serious damage to both individuals and businesses.
A data breach can cause serious damage to both individuals and businesses.
- For Individuals: People lose privacy. Their personal data might be sold on the dark web. Criminals can use it for identity theft, fake accounts, or scams. Recovering from such incidents can take years.
- For Businesses: Companies lose customer trust and face legal fines. Their brand reputation gets damaged. In some cases, small businesses never recover financially from a major breach.
- For Society: When massive amounts of data are exposed, it weakens public trust in digital systems. This affects online transactions, e-commerce, and even government operations.
Data Breach in Cyber Security
In the field of cyber security, data breaches are one of the most serious threats. It not only exposes sensitive data but also reveals system’s weaknesses.
Cybersecurity experts use advanced tools like firewalls, intrusion detection systems, and encryption to prevent such incidents. They also follow strict compliance rules like GDPR and HIPAA to ensure data safety.
Organizations use a data breach tracker to monitor potential leaks or suspicious activities in real time. These trackers can alert security teams before the situation gets worse.
If you follow data breach news, you’ll notice that cyberattacks are becoming more frequent and sophisticated. New ransomware and phishing techniques appear every year, making it harder for businesses to keep up.
Popular Data Breach Trackers and Websites
If you want to check whether your data has been leaked, several websites can help:
- Have I Been Pwned: This popular data breach website lets you check if your email or password has appeared in a known breach.
- Mozilla Monitor: It shows if your personal information has been part of any online leaks.
- Google Data Breach Checker: Many users rely on data breach Google alerts, which notify them if their saved passwords are found on the dark web.
These tools help users stay aware and take action before it’s too late.
How to Prevent Data Breach

Now that we understand the risks, let’s look at how to prevent data breach in simple steps:
- Use Strong, Unique Passwords: Create strong passwords with a mix of letters, numbers, and symbols. Avoid using the same password for multiple accounts.
- Enable Two-Factor Authentication: Two-factor authentication (2FA) adds an extra layer of protection. Even if someone knows your password, they can’t log in without the second step.
- Keep Your Software Updated: Updates often fix security holes. Always keep your operating system, browsers, and apps up to date.
- Educate Employees: If you run a business, conduct regular cybersecurity training. Most breaches happen due to human errors. Awareness is your first line of defense.
- Encrypt Sensitive Data: Encryption converts data into unreadable code. Even if hackers steal it, they can’t use it without the decryption key.
- Use Firewalls and Antivirus Software: A good firewall and antivirus tool can stop many attacks before they start.
- Regular Data Backups: Back up your important data to a secure cloud or offline location. This ensures you can recover it after an attack.
- Stay Updated with Data Breach News: Keeping an eye on data breach news helps you understand new threats and protect yourself better. Cybersecurity blogs, government advisories, and trusted IT websites regularly share updates about major breaches and prevention tips.
“Knowledge is power, and in the digital world, it’s also your best protection.”
Final Thoughts
A data breach can happen to anyone- individuals, startups, or global corporations. But staying informed and following good security practices can make a huge difference.
Always use strong passwords, stay alert for phishing messages, and keep your systems updated. Use tools like data breach trackers and data breach websites to monitor your exposure.
Cybersecurity isn’t just a technical job, it’s a shared responsibility. In a connected world, protecting data means protecting trust, privacy, and the future of digital life.
If your organization is facing the above challenges, please contact our support team to learn how the Assurtiv GRC Tool can help your team achieve Compliance with Minimal Effort and Maximum Benefits.
Here, you can Request for a Demo!



